For additional information, refer to the AnyConnect configuration guide.
Windows 10 Always On Vpn Anyconnect
Client Download
As a mobile worker roaming to different locations, the always-on intelligent VPN efficiently adapts to a tunneling protocol. For example, AnyConnect's Datagram Transport Layer Security (DTLS) thrives in offices that are constantly on VoIP applications. Connect to VPN: Step 1 Open the Cisco AnyConnect application on your computer. In the Start menu, click All Programs Cisco Cisco AnyConnect Secure Mobility Client; Click the Cisco AnyConnect Secure Mobility Client to launch the application. Step 2 Type in vpnconnect.rochester.edu then click Connect. Step 3 Enter your NetID and password.
Cisco Asa Always On Vpn
Unlike the ASA, the MX does not support web deploy or web launch, a feature that allows end users to access a web page on the AnyConnect server to download the AnyConnect client. With the MX, there are download links to the client software on the AnyConnect settings page on the dashboard, however, the download links are only available to the Meraki dashboard admin and not the end user. We do not recommend sharing the down link with users as the link expires after every five minutes of loading the AnyConnect settings page.
We recommend downloading the AnyConnect client directly from Cisco.com as there may be an updated version in the Cisco repository. Refer to the doc for the AnyConnect clientrelease notes. We also recommend using either Meraki Systems Manager, an equivalent MDM solution, or Active Directory to seamlessly push the AnyConnect software client to the end user's device.
AnyConnect requires a VPN client to be installed on a client device. The AnyConnect client for Windows, MacOS, and Linux are available on the Client Connection section of the AnyConnect configuration page on the dashboard and can be downloaded by a Meraki dashboard administrator. Please note, the download links on the Meraki dashboard expire after five minutes. The AnyConnect client for mobile devices can be downloaded via the respective mobile stores. You can also download other versions (must be version 4.8 or higher) of the AnyConnect client from Cisco.com if you have an existing AnyConnect license. AnyConnect web deploy is not supported on the MX at this time.
- Installing the AnyConnect client
- You only need the VPN box checked. Once the client has been installed on the device, open the AnyConnect application and specify the hostname or IP address of the MX (AnyConnect server) you need to connect to.
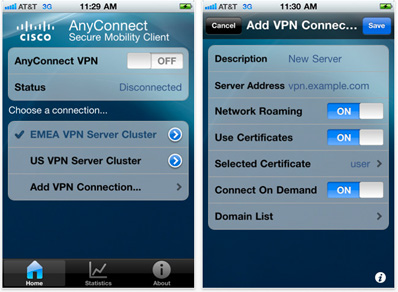
AnyConnect Profiles
An AnyConnect profile is a crucial piece for ensuring easy configuration of the AnyConnect client software, once installed. The MX does not support the use of custom hostnames for certificates (e.g. vpn.xyz.com). The MX only supports use of the Meraki DDNS hostname for auto-enrollment and use on the MX. With the Meraki DDNS hostname (e.g. mx450-xyuhsygsvge.dynamic-m.com) not as simply as a custom hostname, the need for AnyConnect profiles cannot be overemphasized. Profiles can be used to create hostname aliases, thereby masking the Meraki DDNS with a friendly name for the end user.
Cisco AnyConnect client features are enabled in AnyConnect profiles. These profiles can contain configuration settings like server list, backup server list, authentication time out, etc., for client VPN functionality, in addition to other optional client modules like Network Access Manager, ISE posture, customer experience feedback, and web security. It is important to note that at this time, the Meraki MX does not support other optional client modules that require AnyConnect head-end support. For more details, see AnyConnect profiles.
When a profile is created, it needs to get pushed to the end user's device. There are three ways to do this.
1. Through the AnyConnect server (MX): If profiles are configured on the dashboard, the MX will push the configured profile to the user's device after successful authentication.
2. Through an MDM solution: Systems Manager, an equivalent MDM solution, or Active Directory can be used push files to specific destinations on the end user's device. Profiles can also be pushed to the following paths:
Windows
%ProgramData%CiscoCisco AnyConnect Secure Mobility ClientProfile
Mac OS X
/opt/cisco/anyconnect/profile
Linux
/opt/cisco/anyconnect/profile
3. Manually: Profiles can also be preloaded manually to the same paths as listed above.
How to Create a Profile
Profiles can be created using the AnyConnect profile editor. The profile editor can be downloaded from the AnyConnect Settings page on dashboard or on cisco.com. Refer to this link for more details on AnyConnect profiles.
Using the profile editor: The profile editor can be downloaded from the AnyConnect Settings page on dashboard or on Cisco.com. The profile editor only runs on Windows operating systems. The screenshot below shows a configured server ton the Server List Entry option.
When configuration is complete, save the profile. It is recommended to use a unique file name to avoid profile overrides by other AnyConnect servers, then you can upload the file to the profile update section on the AnyConnect settings page.
Please note that only VPN profiles are supported on the MX at this time. This means you cannot push NVM, NAM, or Umbrella profiles via the MX.
- Select enable profiles, upload your xml file, and save your configuration
- After a user successfully authenticates, the configured profile gets pushed to the user's device automatically
- The result of the .xml can be seen below, after successful authentication to the AnyConnect server; this gives users the ease of selecting VPN servers on the AnyConnect client
The Meraki DDNS hostname is not easy to remember, therefore end users are not expected to use it directly. Profiles should be used to make connecting to the AnyConnect server easy for end users.
Some VPNs allow split tunneling, however, Cisco AnyConnect and many other solutions offer a way for network administrators to forbid this. When that happens, connecting to the VPN seals off the client from the rest of the LAN. As it turns out, breaking this seal is not that hard, which can be useful for special cases like performing pentests over a VPN designed for average users.
In our case, we had to use a hardware token that only had drivers for Windows and Mac, while most of our tools run best (and are already installed) on Linux. We started investigating on both supported platforms mentioned above and found
what others have already discovered: the routing table is modified (and kept in this state), while packets are further filtered, probably using kernel hooks.
Both IPv4 and IPv6 are affected by this filtering, and traffic towards additional network interfaces also got redirected. So we embarked on a quest to find what could be done within the rules imposed by the VPN vendor. Our first stop was the gateway in our LAN towards the internet – and thus towards the VPN concentrator. The VPN client explicitly installed routes to keep that reachable, however, packets sent directly towards the LAN gateway never arrived there, leading us towards the idea of further kernel-based filters.
The next idea was the VPN server itself since it had to be able to receive packets from the clients as part of normal operation. However, the question is: how can you tell the packets apart on the gateway – as you still have to forward packets that are part of the normal VPN operator towards the VPN server. The trivial way was TCP port numbers, so we tried connecting to various TCP ports on the VPN server, but the gateway saw no SYN packets.
This left us with a single opportunity: keeping even the TCP port the same as the port used by the tunnel already. As netstat has shown, a TCP connection towards port 443 was kept open throughout the VPN session, and subsequent connections were allowed by the
filtering mentioned above – we could even see these SYN packets on the gateway. The only problem was to tell TCP streams apart at the gateway so that the VPN still worked while we could initiate connections outside of it at the same time.
And then it clicked: while trying to cope with the fact that many public (or semi-public) Wi-Fi networks filter everything besides TCP/443 (HTTPS), we had SSLH deployed to multiplex HTTPS and SSH on the same TCP port. This works reliably because they are really easy to tell apart upon the first packet:
- SSH clients send plain text one-liners that identify the protocol and client version, while
- SSL/TLS clients send binary Client Hello packets that identify the protocol version and supported ciphers.
SSH fits this case since its port forwarding features makes it possible to punch as many holes as necessary, regardless of the direction (VPN to LAN vs. LAN to VPN).
On Debian and its derivative systems, SSLH can be installed simply from the package with the same name (sslh) and configuration can be found in the file /etc/default/sslh as a command line, as this is where SSLH takes its options from. Below is the significant line:
This just means that SSLH listens on the internal (LAN) IP address of the gateway and based on the first packet received from a client that reaches this port, it either forwards it to
- a local SSH server (here we had the VPN client running on a Windows VM, and the Linux host had the SSH daemon running, hence the variable name
$VM_HOST_IP) or - the original VPN server.
Changes to the options can be applied under Debian and its derivatives by running /etc/init.d/sslh restart and the results can be tested in isolation first by connecting to TCP port 443 of the gateway, which should behave like the VPN server when using a TLS client like openssl s_client and act as an SSH server when using OpenSSH or PuTTY.
When all this works, the last bit is to redirect traffic towards the VPN server to SSLH. One way is using NAT functionality from iptables:
This command adds a rule to the chain called PREROUTING within the nat table, where packets arrive before the routing decision happens. The next part is the filter, which is important to avoid loops: we only apply the magic to packets where the network interface that the packet arrives through is the LAN interface. The rest narrows the filter further to the destination TCP port being 443 and the destination host being the VPN server. The last part is what happens when this rule matches: we invoke the REDIRECT target that rewrites
- the destination host to the IP address of the interface the packet arrived through (here: LAN interface) and
- the destination port to the one supplied (here: 443).

AnyConnect Profiles
An AnyConnect profile is a crucial piece for ensuring easy configuration of the AnyConnect client software, once installed. The MX does not support the use of custom hostnames for certificates (e.g. vpn.xyz.com). The MX only supports use of the Meraki DDNS hostname for auto-enrollment and use on the MX. With the Meraki DDNS hostname (e.g. mx450-xyuhsygsvge.dynamic-m.com) not as simply as a custom hostname, the need for AnyConnect profiles cannot be overemphasized. Profiles can be used to create hostname aliases, thereby masking the Meraki DDNS with a friendly name for the end user.
Cisco AnyConnect client features are enabled in AnyConnect profiles. These profiles can contain configuration settings like server list, backup server list, authentication time out, etc., for client VPN functionality, in addition to other optional client modules like Network Access Manager, ISE posture, customer experience feedback, and web security. It is important to note that at this time, the Meraki MX does not support other optional client modules that require AnyConnect head-end support. For more details, see AnyConnect profiles.
When a profile is created, it needs to get pushed to the end user's device. There are three ways to do this.
1. Through the AnyConnect server (MX): If profiles are configured on the dashboard, the MX will push the configured profile to the user's device after successful authentication.
2. Through an MDM solution: Systems Manager, an equivalent MDM solution, or Active Directory can be used push files to specific destinations on the end user's device. Profiles can also be pushed to the following paths:
Windows
%ProgramData%CiscoCisco AnyConnect Secure Mobility ClientProfile
Mac OS X
/opt/cisco/anyconnect/profile
Linux
/opt/cisco/anyconnect/profile
3. Manually: Profiles can also be preloaded manually to the same paths as listed above.
How to Create a Profile
Profiles can be created using the AnyConnect profile editor. The profile editor can be downloaded from the AnyConnect Settings page on dashboard or on cisco.com. Refer to this link for more details on AnyConnect profiles.
Using the profile editor: The profile editor can be downloaded from the AnyConnect Settings page on dashboard or on Cisco.com. The profile editor only runs on Windows operating systems. The screenshot below shows a configured server ton the Server List Entry option.
When configuration is complete, save the profile. It is recommended to use a unique file name to avoid profile overrides by other AnyConnect servers, then you can upload the file to the profile update section on the AnyConnect settings page.
Please note that only VPN profiles are supported on the MX at this time. This means you cannot push NVM, NAM, or Umbrella profiles via the MX.
- Select enable profiles, upload your xml file, and save your configuration
- After a user successfully authenticates, the configured profile gets pushed to the user's device automatically
- The result of the .xml can be seen below, after successful authentication to the AnyConnect server; this gives users the ease of selecting VPN servers on the AnyConnect client
The Meraki DDNS hostname is not easy to remember, therefore end users are not expected to use it directly. Profiles should be used to make connecting to the AnyConnect server easy for end users.
Some VPNs allow split tunneling, however, Cisco AnyConnect and many other solutions offer a way for network administrators to forbid this. When that happens, connecting to the VPN seals off the client from the rest of the LAN. As it turns out, breaking this seal is not that hard, which can be useful for special cases like performing pentests over a VPN designed for average users.
In our case, we had to use a hardware token that only had drivers for Windows and Mac, while most of our tools run best (and are already installed) on Linux. We started investigating on both supported platforms mentioned above and found
what others have already discovered: the routing table is modified (and kept in this state), while packets are further filtered, probably using kernel hooks.
Both IPv4 and IPv6 are affected by this filtering, and traffic towards additional network interfaces also got redirected. So we embarked on a quest to find what could be done within the rules imposed by the VPN vendor. Our first stop was the gateway in our LAN towards the internet – and thus towards the VPN concentrator. The VPN client explicitly installed routes to keep that reachable, however, packets sent directly towards the LAN gateway never arrived there, leading us towards the idea of further kernel-based filters.
The next idea was the VPN server itself since it had to be able to receive packets from the clients as part of normal operation. However, the question is: how can you tell the packets apart on the gateway – as you still have to forward packets that are part of the normal VPN operator towards the VPN server. The trivial way was TCP port numbers, so we tried connecting to various TCP ports on the VPN server, but the gateway saw no SYN packets.
This left us with a single opportunity: keeping even the TCP port the same as the port used by the tunnel already. As netstat has shown, a TCP connection towards port 443 was kept open throughout the VPN session, and subsequent connections were allowed by the
filtering mentioned above – we could even see these SYN packets on the gateway. The only problem was to tell TCP streams apart at the gateway so that the VPN still worked while we could initiate connections outside of it at the same time.
And then it clicked: while trying to cope with the fact that many public (or semi-public) Wi-Fi networks filter everything besides TCP/443 (HTTPS), we had SSLH deployed to multiplex HTTPS and SSH on the same TCP port. This works reliably because they are really easy to tell apart upon the first packet:
- SSH clients send plain text one-liners that identify the protocol and client version, while
- SSL/TLS clients send binary Client Hello packets that identify the protocol version and supported ciphers.
SSH fits this case since its port forwarding features makes it possible to punch as many holes as necessary, regardless of the direction (VPN to LAN vs. LAN to VPN).
On Debian and its derivative systems, SSLH can be installed simply from the package with the same name (sslh) and configuration can be found in the file /etc/default/sslh as a command line, as this is where SSLH takes its options from. Below is the significant line:
This just means that SSLH listens on the internal (LAN) IP address of the gateway and based on the first packet received from a client that reaches this port, it either forwards it to
- a local SSH server (here we had the VPN client running on a Windows VM, and the Linux host had the SSH daemon running, hence the variable name
$VM_HOST_IP) or - the original VPN server.
Changes to the options can be applied under Debian and its derivatives by running /etc/init.d/sslh restart and the results can be tested in isolation first by connecting to TCP port 443 of the gateway, which should behave like the VPN server when using a TLS client like openssl s_client and act as an SSH server when using OpenSSH or PuTTY.
When all this works, the last bit is to redirect traffic towards the VPN server to SSLH. One way is using NAT functionality from iptables:
This command adds a rule to the chain called PREROUTING within the nat table, where packets arrive before the routing decision happens. The next part is the filter, which is important to avoid loops: we only apply the magic to packets where the network interface that the packet arrives through is the LAN interface. The rest narrows the filter further to the destination TCP port being 443 and the destination host being the VPN server. The last part is what happens when this rule matches: we invoke the REDIRECT target that rewrites
- the destination host to the IP address of the interface the packet arrived through (here: LAN interface) and
- the destination port to the one supplied (here: 443).
Since SSLH was configured to listen on TCP port 443 on the LAN interface, this results in the same effect as in the above SSLH testing scenario, where we connected directly to TCP port 443 on the gateway. And the best part is that the NAT solution provided by iptables is fully bidirectional, reply packets from SSLH are automatically translated back to make it seems as if they were sent by the VPN server.
So with the iptables rule in place, everything is ready for a real-life test. The progress of SSLH can be followed in syslog and as it can be seen below, after the AnyConnect client has connected properly, SSH connections can also get through, and everything gets routed to its proper destination.

